Since we now live in a digital world, it’s easy to commit a cybercrime. Statistics show that 2,244 cybercrimes are committed every single day.
Social engineering is a technique used by scammers and hackers to trick their targets into divulging personal information by appealing to their emotions. Those who fall victim to these data breaches may lose a great deal of money.
This article will discuss the various forms of social engineering and provide advice on how to avoid becoming a victim.
How forex trading accounts are hacked
1. Phishing
Criminals use phishing, also known as “spoofing,” to trick users into giving up sensitive information by making it appear as though the sender is from a trusted source.
Typically, victims are duped into divulging personal information, such as passwords and banking details, by receiving emails that appear to have come from a legitimate source but actually originate from a malicious domain.
2. Keylogging
The practice of secretly recording keyboard input is known as keylogging. Scammers frequently use a keylogger tool, either a computer program or a hardware device, to record the user’s keystrokes for later illegal use. Phishing attacks and remote downloads are common ways for hackers to install software keyloggers on your device without your knowledge. Some software keyloggers can also record what is copied to the clipboard and save screenshots of your computer’s screen. Antivirus programs can identify and eliminate these keyloggers. When a hardware keylogger is built into or attached to your device, it can be difficult to detect. In contrast to software keyloggers, these keyloggers would go undetected by antivirus programs.
3. Man-in-the-middle attack
The convenience of free public WiFi in every location comes with potential downsides. Man-in-the-middle (MitM) attacks can happen on public WiFi networks.
A man in the middle (MitM) attack occurs when a hacker poses as a trusted intermediary in order to steal sensitive information. A malicious third party could potentially hijack a user’s browser and direct them to a fraudulent website whenever they try to access a legitimate one.
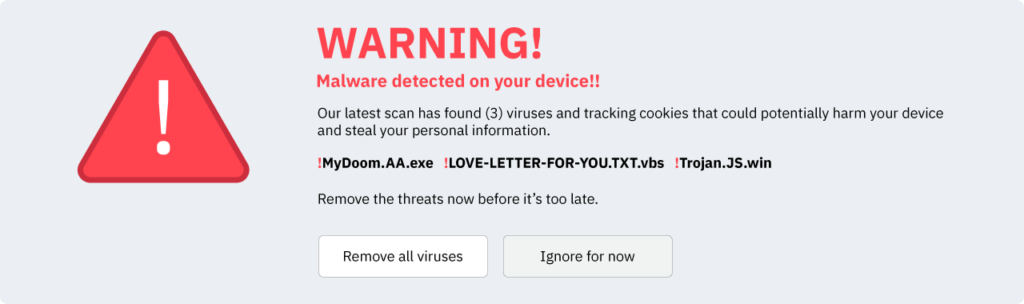
4. Scareware
Scareware is malicious software designed to frighten its targets. Scammers use fake warnings to scare victims into downloading malware or visiting compromised websites.
An alarmist message like this one:
5. Baiting
How often do you get emails promising delivery of purchases you never made? If so, a con artist may have been trying to catch you off guard. Con artists who employ this strategy rely on their victims’ natural tendencies toward curiosity or greed.
If a website asks you to create an account before allowing you to download anything (ebooks, music, or movies), you should be wary. The information you provide is gold to con artists. Malware can be hidden in downloaded files and used to steal sensitive information.
Physical forms of baiting are also possible. Keep moving if you come across an unattended USB device or external hard drive. Con artists spread malware by leaving infected devices lying around, hoping that unsuspecting victims will plug them in and let the infection spread.
How to protect your forex trading account
1. For starters, you shouldn’t click on random links.
Always check to see that the URL starts with “HTTPS” rather than “HTTP,” and pay close attention to any spelling mistakes or strange characters it may contain. Do not enter your personal information on any website that does not start with HTTPS, or that uses an incorrect spelling of the word “Deriv,” which is our official website.
If you get an email that appears to be from a reputable company but asks you to verify your account information on a different website, you should not click on the link provided. Don’t follow any links that take you elsewhere on the Internet.
2. Verify the accuracy of the message’s contents.
It’s important to carefully read all incoming emails and messages to make sure they accurately reflect the sender’s intended tone and content. Check for grammatical and spelling mistakes as well. All of us at the genuine article take great care in crafting our messages before sending them to you.
See anything out of the ordinary? You can verify if the email is a phishing attempt by pasting its contents into a search engine, or you can get in touch with the sender via phone or another email address to see if it was a mistake.
Only no-reply@deriv.com or support@deriv.com will be used to contact you by Deriv. You should therefore notify us via live chat if you receive an email from us that did not originate from these addresses.
3. To protect yourself, number three, use barriers.
Keep your OS and anti-virus software up to date. If you want to take advantage of the latest features and bug fixes, you should always use the most recent versions of your favorite apps and browser.
If you are accessing sensitive information while conducting business with us, we advise using a Virtual Private Network (VPN) to encrypt your connection.
4. Disable any automatic connection features.
Stopping MitM attacks requires disabling auto-connect for WiFi and Bluetooth on all of your devices. When you aren’t using your network, it’s best to disable it.
We advise against using public WiFi due to the risk of being tricked into connecting to a malicious network. Verify the WiFi credentials to make sure you’re connecting to a legitimate, secure, and reputable public WiFi network.
5. choose a robust password.
Passwords are case-sensitive and should be a combination of uppercase and lowercase letters, numbers, and special characters. Don’t include any identifying details like that on here.
Passwords should be changed frequently, and you should avoid using the same password for different online services. Password managers not only store your passwords for you but also suggest ones that are both secure and easy to remember.
Furthermore, turn on two-factor authentication via your email or mobile device. Password-protected accounts aren’t the most secure, so it’s a good idea to use 2FA alongside it.
6. Pay attention to what’s going on around you.
Keep an eye on your stuff at all times. Always keep your electronics in plain sight and keep an eye out for strange or unfamiliar electronics to reduce the risk of keylogger infection or implantation.
Don’t be too nosy and start poking around on any random USB drives or external hard drives you might find. You wouldn’t knowingly let malicious software onto your device, would you?